Active Directory Audit
An AD (Active Directory) security audit evaluates the security setup of your Active Directory environment to identify vulnerabilities and ensure compliance with best practices.
-
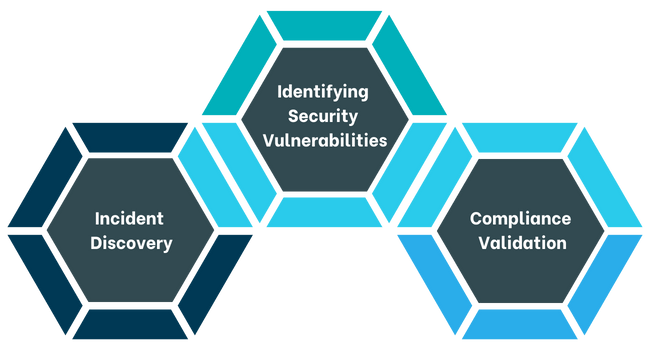
Identifying Security Vulnerabilities: An Active Directory (AD) audit helps identify potential security vulnerabilities and weaknesses, such as weak password policies, misconfigured access permissions, or outdated and unused accounts. By detecting these risks early, organizations can take swift corrective actions, effectively reducing the likelihood of potential security breaches.
-
Compliance Validation: Many industry standards and regulations (such as GDPR, SOC2, HIPAA, ISO27001) require IT systems to meet specific security and compliance criteria. An AD audit ensures that the system adheres to these regulations, helping to avoid fines and legal issues.
-
Maintaining Data Privacy and Security: An AD audit ensures that access to sensitive data is properly restricted, allowing only authorized users to gain entry. This significantly reduces the risk of data theft and loss, enhancing overall data protection.
-
Incident Discovery: AD audits assist in the early detection and investigation of IT incidents. By analyzing log files and access events, audits help identify suspicious activities and support the implementation of appropriate responses.
Why is an Active Directory audito important?
Active Directory (AD) is the backbone of an organization’s IT infrastructure, managing user authentication, permissions, and access to critical resources. If misconfigured, it can expose the company to severe security vulnerabilities, potentially leading to data breaches, unauthorized access, and operational disruptions, which could ultimately cripple the business.
The process
An AD audit typically involves the following steps:
-
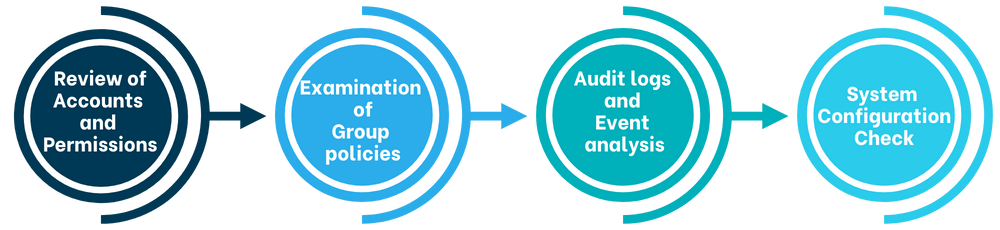
Review of Accounts and Permissions: User and service accounts, along with their assigned permissions, are analyzed. Accounts with excessive permissions and inactive or unused accounts are identified.
-
Examination of Group Policies: Group Policy Objects (GPOs) are reviewed to ensure they meet security requirements and organizational policies.
-
Audit Logs and Event Analysis: Security logs and events are analyzed to detect suspicious activities, such as repeated failed login attempts or unauthorized access attempts.
-
System Configuration Check: The settings of servers and services are reviewed to ensure they are configured securely and in line with best practices.
Deliverable
You’ll receive a detailed report highlighting vulnerabilities and recommendations for improving your Active Directory security.
-
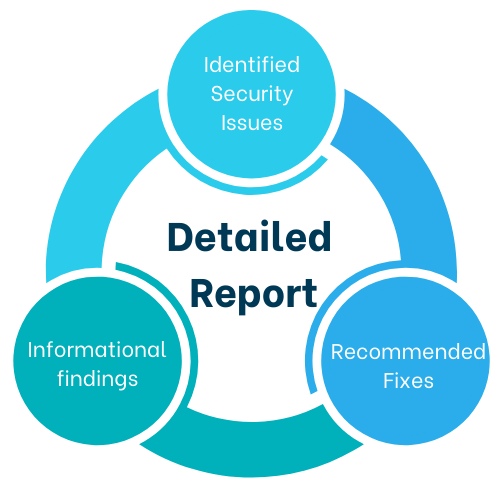
Identified Security Issues: Critical vulnerabilities and misconfigurations that pose a direct risk to your environment.
-
Informational Findings: Non-critical areas for improvement, such as outdated configurations or practices that could enhance performance and security but don’t currently pose a security threat.
-
Recommended Fixes: A detailed action plan with clear steps for addressing each issue, from tightening access controls to adjusting group policies, along with best practice recommendations to strengthen your overall security posture.
If needed, we can assist in the remediation process, offering expert guidance to your IT team on implementing the recommended fixes. We will also validate the changes to ensure they effectively address the identified issues and enhance your security posture.