Cloud Security Posture hardening
Cloud Security Posture Hardening is the process of enhancing the security of a cloud environment by configuring and reinforcing security controls to reduce vulnerabilities and minimize risks. This involves implementing best practices such as tightening access permissions, securing data storage, enforcing encryption, monitoring network traffic, and regularly applying updates and patches. The goal is to create a robust security framework that minimizes potential attack vectors and protects the organization’s cloud assets from unauthorized access, data breaches, and other threats. By hardening their cloud security posture, organizations can safeguard sensitive data and ensure a resilient and compliant cloud environment.
This service helps organizations secure their cloud environments by proactively strengthening configurations and reducing security risks.
-
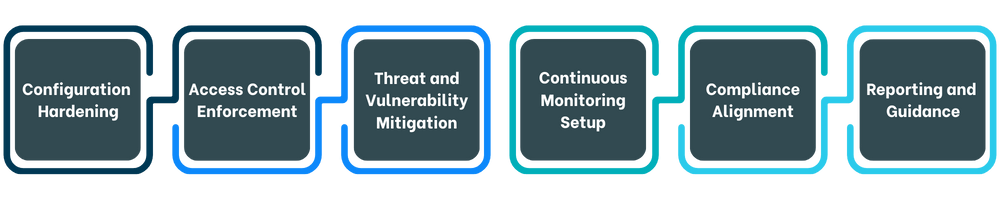
Configuration Hardening: Strengthens security by configuring cloud assets to follow industry best practices.
-
Access Control Enforcement: Implements strict access permissions and role-based access to minimize unauthorized access.
-
Threat and Vulnerability Mitigation: Identifies and remediates vulnerabilities, misconfigurations, and excessive permissions.
-
Continuous Monitoring Setup: Establishes logging and monitoring to detect unusual activity and respond to threats in real-time.
-
Compliance Alignment: Ensures cloud configurations meet regulatory and industry security standards.
-
Detailed Reporting and Guidance: Provides a summary of improvements and detailed recommendations for ongoing security posture maintenance.
-
Improved Cloud Security Resilience: Reduces risks and strengthens defenses, ensuring a robust and compliant cloud environment.