GAP Assessment
Comprehensive evaluation of an organization’s security practices against industry-leading standards like ISO 27001, NIS2, SOC2, HIPAA, and ISO 42001. It identifies potential vulnerabilities and provides tailored recommendations to ensure compliance and mitigate risks.
Are you compliant with compliance security standards?
With a gap assessment you can get a clear picture of whether your company’s security processes are compliant with the major security compliance certifications such as ISO 27001, SOC2, HIPAA, NIS2, ISO 42001.
Why is a Gap Assessment Crucial?
In today’s digital age, protecting your company’s data and reputation is more important than ever. A gap assessment is like a security checkup for your business. It helps you identify weaknesses in your security posture and points out the fields for improvement.
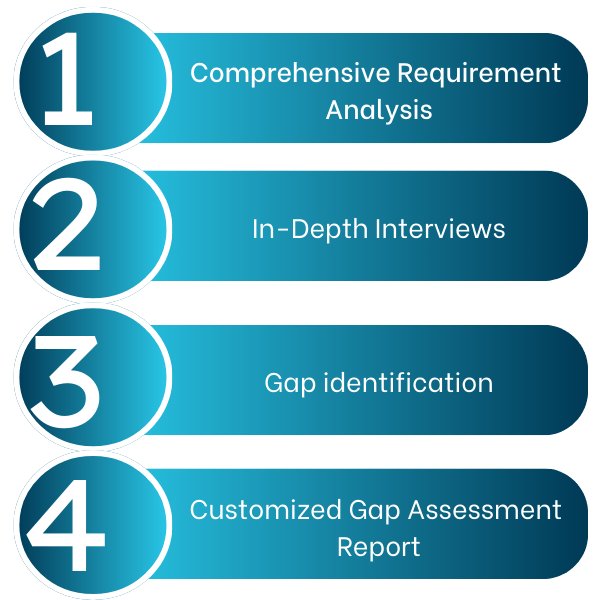
How Does Our Gap Assessment Process Work?
-
Comprehensive Requirements Analysis: We’ve meticulously studied the requirements of industry-leading standards like SOC 2, ISO 27001, NIS2, HIPAA, and ISO 42001. Our assessment is based on a comprehensive requirement list that covers every aspect of your security infrastructure.
-
In-Depth Interviews: Our security experts will conduct detailed interviews with key personnel within your organization. We’ll delve into your internal processes, technology infrastructure, and external environment to gain a complete understanding of your operations.
-
Gap Identification: By comparing your current practices to the industry standards, we’ll pinpoint areas where your security falls short. This could include vulnerabilities in your network, inadequate data encryption, or insufficient employee training and so on.
-
Customized Gap Assessment Report: We’ll provide a detailed report outlining the identified security gaps and their potential consequences. The report will also include recommendations for remediation and improvement.
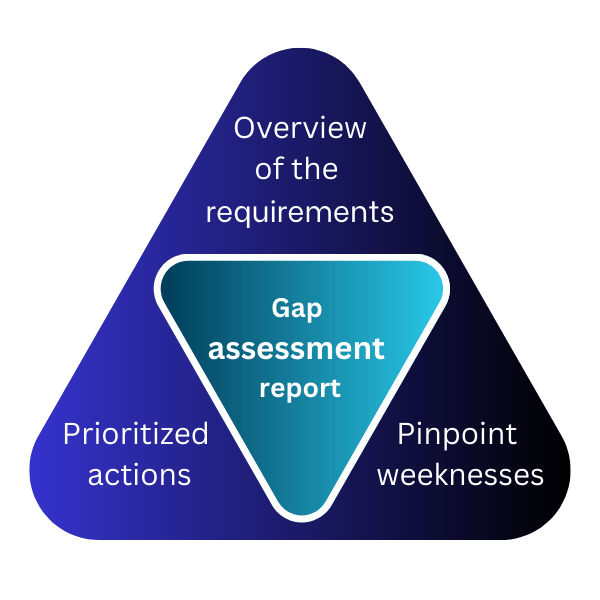
What Can You Expect from Our Gap Assessment?
-
Clear Overview of Certification Requirements: Our assessment will provide a detailed overview of the specific security requirements and controls that are necessary to achieve your desired certification (e.g., SOC 2, ISO 27001, NIS2, HIPAA, ISO 42001). This will help you understand the scope of the certification process and the steps you need to take to achieve it.
-
Pinpoint Weaknesses: The table will clearly identify areas where your security measures fall short of industry standards.
-
Prioritized Actions: We’ll prioritize the most critical areas for improvement, ensuring you focus on the most pressing issues.

Why Choose Us?
-
Deep Expertise: Our team of security professionals has extensive experience in conducting gap assessments and - helping organizations improve their security posture.
-
Customized Approach: We tailor our assessments to meet the unique needs of your business, ensuring that we address the most critical areas of concern.
-
Results-Oriented Focus: Our goal is to help you achieve a strong security posture and minimize your risk exposure.