Penetration testing
In today’s digital landscape, relying solely on standard security measures is no longer sufficient. Cyber threats evolve every day, with attack techniques advancing rapidly. Beyond a full scale pentration test the security can be further enhanced through specialized services we provide like Attack Surface Monitoring (ASM) which provides continuous visibility into your external exposure through passive and minimal active scans or Vulnerability Scanning which unlike penetration testing, vulnerability scanning identifies all known vulnerabilities on your systems or a simple Web Application Test. At Vendito Security our penetration testing approach is about staying ahead. We don’t just follow the basic standards we continually track the latest attack trends and hacking and hacking methods to uncover multiple attack paths that could compromise your system. This way, we are not only identifying risks but actively helping you close the gaps before any malicious actor finds them.
Why is Penetration Testing More Important Than Ever?
In our increasingly interconnected world, cybersecurity threats are evolving at an alarming rate. Cybercriminals are employing advanced techniques to exploit vulnerabilities in systems and networks. To safeguard sensitive data and maintain business continuity, organizations must prioritize robust security measures. For this reason several security standards and certifications commonly mandate penetration testing as a requirement (SOC2, ISO 27001, FedRAMP, HIPAA, PCI DSS, NIS2)
Penetration testing, often referred to as “pentesting,” is a controlled cyberattack designed to find and exploit weaknesses in your system. Think of it as a simulated real-world attack. The objective to expose vulnerabilities that hackers could exploit so that we can secure them before they’re discovered by someone with malicious intent.
Ransomware groups, like well-known threat actors LockBit, Conti and others now run their own “penetration testing” teams. These black-hat hacking teams specialize in gaining initial access or maintaining persistence to corporate networks. Often they are using advanced penetration testing techniques not just phishing to breach defenses undetected. This is why it’s so crucial that companies don’t rely on ad hoc security but work with skilled, ethical penetration testing professionals who can identify weaknesses before cybercriminals do. With a trusted and specialized offensive security team, you are not only guarding against general risks but you are preparing for the specific tactics used by the most threat actors.
Every company with an online presence is a potential target. Hackers constantly look for weak points to access sensitive information, disrupt services, or even demand ransoms. A penetration test doesn’t just find these vulnerabilities; it helps you fix them before anyone can exploit them. Through pentesting, you’re actively protecting your reputation, data, and clients from cyber threats.
Our team is committed to staying at the forefront of cybersecurity. We have multiple certifications like OSCP, OSCE, and more, ensuring a high standard of technical skill. Beyond certifications, our experts regularly participate in cybersecurity competitions and rank highly on training platforms, demonstrating our commitment to staying sharp and up-to-date on the latest offensive techniques. This dedication to training and excellence means we’re always prepared to tackle the most sophisticated security challenges.
Unlike many providers, we don’t just tick boxes on a checklist. We actively adapt to the latest attack methods, which means our testing is relevant and thorough. Our team investigates multiple attack paths, exposing areas that might otherwise be overlooked. By staying at the forefront of cybersecurity trends, we ensure our clients are protected against the newest forms of attack.
How Penetration Testing Works
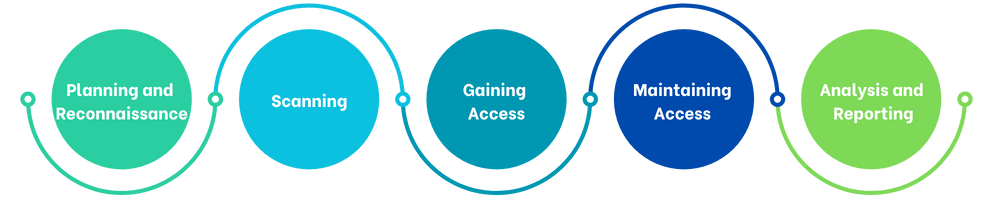
Our penetration testing process involves several critical stages:
-
Planning and Reconnaissance
We begin by understanding your system and gathering information, such as potential entry points and user details. This allows us to plan an effective attack strategy. -
Scanning
At this stage, we use specialized tools to analyze how your system responds to different types of intrusion attempts. This helps us to identify the weaknesses that need addressing. -
Gaining Access
This is where we simulate real attacks by trying to access your system using various hacking techniques. The goal is to exploit vulnerabilities to assess their potential impact. -
Maintaining Access
If we gain access, we test the system’s response to a prolonged presence, simulating the actions of an attacker trying to maintain a foothold in your network. -
Analysis and Reporting
After the test, we provide a detailed analysis of our findings, highlighting the vulnerabilities we identified, the level of risk they pose, and how they can be fixed.
Going Beyond Standards
Our commitment to quality means we not only assess your system based on standard guidelines but also explore the latest attack techniques, finding weaknesses others might miss. Whether it’s uncovering hidden attack paths or assessing emerging threats, our focus is on comprehensive protection.
Web Application Penetration Testing
Web Application Penetration Testing Service offers organizations a proactive approach to securing their web applications by identifying and addressing vulnerabilities that attackers could exploit. Testing options include Black Box, Gray Box, and White Box methodologies:
-
Black Box: Testers simulate external attacks with no prior knowledge of the application, uncovering vulnerabilities from an outsider’s perspective.
-
Gray Box: Testers operate with partial knowledge, such as user credentials, to identify security weaknesses that might be exploited by internal users with limited access.
-
White Box: Testers have full visibility into the application’s code and architecture, enabling a deep and comprehensive assessment of security vulnerabilities.
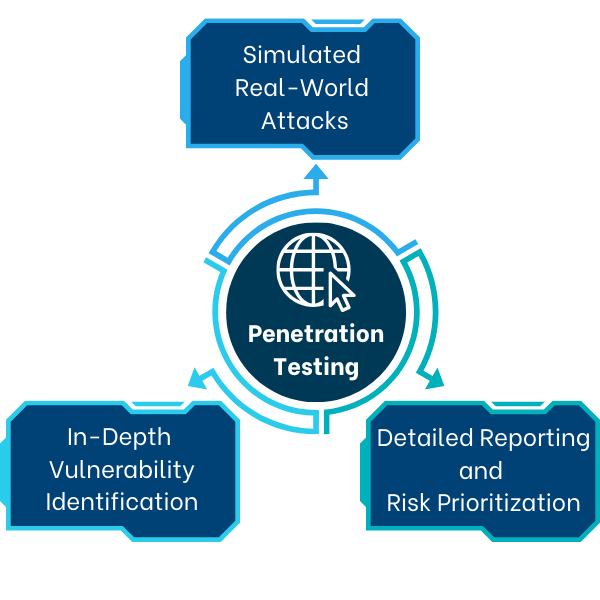
Key Service Components:
-
Simulated Real-World Attacks: Uses real-world attack techniques in each testing category to assess resilience and uncover vulnerabilities across access controls, authentication, and data handling.
-
In-Depth Vulnerability Identification: Combines automated tools with expert manual testing for a thorough evaluation, addressing common issues like injection flaws, session management risks, and insecure configurations.
-
Detailed Reporting and Risk Prioritization: Provides comprehensive reports with findings, risk levels, and guidance on remediation steps, with vulnerabilities ranked by severity to facilitate focused mitigation efforts.
Mobile Application Penetration Testing
This service helps protect mobile applications by proactively identifying and addressing potential security gaps before attackers can exploit them. Static Testing: Analyzes source code, app architecture, and configuration files to uncover security vulnerabilities.
-
Dynamic Testing: Assesses the app’s behavior in a live or simulated environment, simulating attacker techniques to detect runtime vulnerabilities like improper session management, weak authentication, and insecure network communications. Uses automated tools for efficiency and manual expert analysis for thorough and nuanced vulnerability identification.
-
Detailed Reporting and Risk Prioritization: Provides comprehensive reports that include findings, risk assessments, and actionable remediation steps, prioritizing vulnerabilities based on severity to support focused remediation efforts.
Physical Penetration Testing
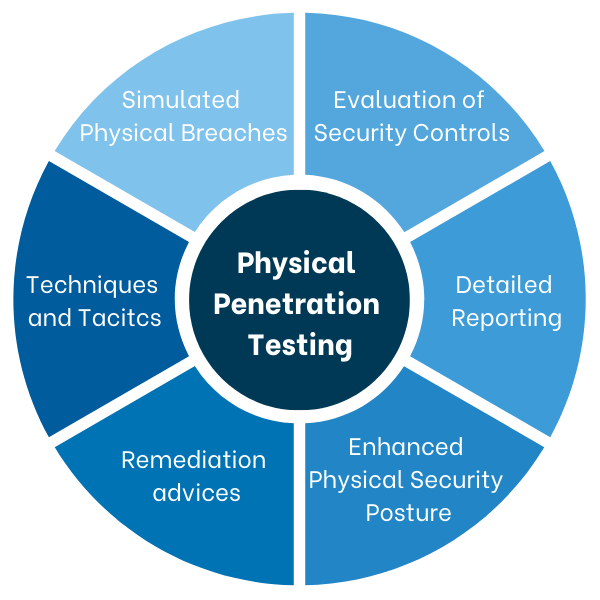
This service helps organizations identify and address physical security weaknesses, reducing the risk of unauthorized access to critical areas.
-
Simulated Physical Breaches: Tests physical security by attempting controlled unauthorized access to facilities.
-
Evaluation of Security Controls: Assesses the effectiveness of security measures like access points, surveillance, and personnel protocols.
-
Techniques and Tactics: Uses methods such as social engineering, lock-picking, and evasion tactics to identify vulnerabilities.
-
Detailed Reporting: Provides insights on weaknesses and areas where physical security can be improved.
-
Remediation Recommendations: Offers actionable steps to strengthen physical security measures and prevent unauthorized access.
-
Enhanced Physical Security Posture: Helps organizations ensure robust protection against physical intrusions.
Social Engineering Testing
This service strengthens an organization’s human defenses by identifying and addressing gaps in employee security awareness.
-
Simulated Social Engineering Attacks: Conducts controlled, realistic social engineering scenarios to identify security awareness gaps.
-
Detection and Response Evaluation: Assesses how well employees recognize and report social engineering attempts.
-
Detailed Reporting: Delivers insights into employee susceptibility, recurring vulnerabilities, and key areas for targeted training.
-
Remediation and Training Recommendations: Suggests targeted awareness training to improve recognition and resistance to manipulation tactics.
-
Strengthened Human Security Layer: Reduces risks by enhancing the organization’s defenses against human-targeted threats.