Vulnerability Scanning and Assessment
Vulnerability scanning
Vulnerability scanning is a security practice that involves systematically examining systems, networks, and applications to identify potential weaknesses or vulnerabilities. This automated process detects known security issues, such as outdated software, misconfigurations, or open ports, that attackers could exploit. By regularly conducting vulnerability scans, organizations can gain insights into their security posture, prioritize risks, and take corrective actions to address potential threats, helping to maintain a secure and resilient IT environment.
This service helps organizations manage security risks proactively by identifying and addressing vulnerabilities before attackers can exploit them.

- Automated Scanning: Regularly scans networks, systems, and applications to detect the latest security vulnerabilities.
- Continuous Monitoring and Reporting: Offers ongoing monitoring, with reports which rate vulnerabilities by severity and provides actionable recommendations for fixing detected vulnerabilities.
Vulnerability Assessment
A vulnerability assessment is a comprehensive evaluation process that identifies, quantifies, and prioritizes security vulnerabilities across an organization’s systems, networks, and applications. Unlike simple scanning, this assessment involves analyzing potential impacts, risk levels, and the effectiveness of existing security controls. The goal is to provide actionable insights for mitigating identified weaknesses and to enhance the organization’s security posture. By regularly conducting vulnerability assessments, organizations can proactively address security gaps and reduce their exposure to potential cyber threats.
This service enables organizations to identify, prioritize, and address security weaknesses, improving resilience and reducing risk exposure.
-
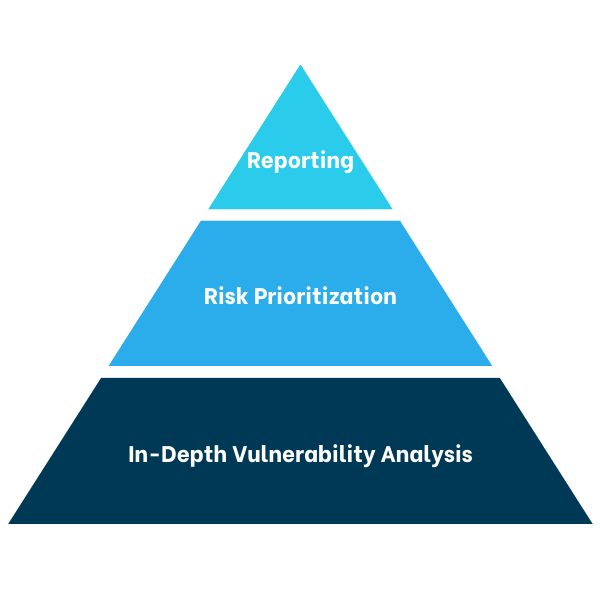
Comprehensive Reporting: Provides detailed reports with insights into vulnerabilities, trends, and security gaps which offers actionable steps and best practices for addressing identified vulnerabilities.
-
Risk Prioritization: Evaluates vulnerabilities based on severity and potential impact, enabling focused remediation.
-
In-Depth Vulnerability Analysis: Conducts comprehensive scans and assessments across networks, systems, and applications.